The Threshold Network has partnered with Immunefi, a leading decentralized finance (DeFi) security platform, to launch a new bug bounty program aimed at improving the security of the Threshold Network. With bounties up to $500k in rewards available, this program incentivizes “white hat” hackers to identify and report potential vulnerabilities in the network's protocols and smart contracts, and you can see full details here: https://immunefi.com/bounty/thresholdnetwork/
This partnership between the Threshold Network and Immunefi highlights the importance of security in the DeFi industry, and underscores our commitment to making the Threshold network as secure as possible.
The Importance of White Hat Work in Open Source Protocols
Security is of utmost importance in open source protocols, as they are often used to handle sensitive data and financial transactions. Any vulnerability or flaw in the protocol can be exploited by malicious actors to compromise the security of the system and cause significant financial losses. As a result, it is essential that open source protocols undergo rigorous testing to ensure they are secure and resilient against potential attacks.
White hat work plays a crucial role in this process, as it involves ethical hacking to identify and report vulnerabilities in the protocol. White hat hackers, also known as ethical hackers, are skilled security professionals who use their expertise to identify weaknesses in software systems and report them to the appropriate parties. This work is essential in preventing malicious actors from exploiting vulnerabilities and causing harm to the system and its users.
Open source protocols rely on a community of developers and security researchers to ensure their security. A robust bug bounty program can help incentivize security researchers to identify and report potential vulnerabilities in the protocol. This process not only helps to identify and fix security issues but also helps to build trust in the protocol by demonstrating a commitment to security and transparency.
Losses in DeFi
Decentralized finance has emerged as a promising alternative to traditional finance, offering users greater transparency, control, and accessibility. However, this nascent ecosystem is not immune to security vulnerabilities, as evidenced by the growing number of DeFi exploits and their devastating impact on users. From flash loan attacks to smart contract bugs, these exploits have resulted in billions of dollars in losses. One way to mitigate some of the risk of exploits is through a good bug bounty program. By incentivizing ethical hackers to find and report vulnerabilities, DeFi platforms can identify and address security issues before they are exploited by malicious actors. A well-designed bug bounty program can not only improve the overall security posture of DeFi platforms but also foster a culture of responsible disclosure within the community.
Chainsec.io reports that as of April 27, 2023 that 134 exploits in DeFi have resulted in $4.26 Billion of losses.

tBTC: the Importance of Security
tBTC is a decentralized, trust-minimized protocol that enables users to use Bitcoin in Ethereum-based DeFi applications. This protocol is important because it provides users with access to the liquidity and flexibility of DeFi while also allowing them to maintain exposure to Bitcoin, the largest and most valuable cryptocurrency.
Given the financial stakes involved in using tBTC, it is crucial to ensure that the protocol is secure and free from vulnerabilities. A white hat bug bounty program is an essential tool in achieving this goal, as it provides an incentive for security researchers to identify and report potential vulnerabilities in the protocol. By proactively identifying and addressing vulnerabilities, the protocol can be made more secure and resilient, ultimately protecting the users who rely on it.
A successful bug bounty program can also help build trust in the protocol by demonstrating a commitment to security and transparency. This can attract more users to the platform and increase the liquidity available for DeFi applications, ultimately helping to drive growth and innovation in the DeFi ecosystem. Therefore, a white hat bug bounty program protecting tBTC is essential to ensuring the long-term success and sustainability of the protocol.
An Introduction to the Immunefi Bug Bounty Program
Immunefi provides comprehensive security coverage for various assets such as smart contracts, websites, and applications. To ensure that the threats to these assets are appropriately addressed, Immunefi has implemented a 5-level scale ranging from "None" to "Critical." This classification system helps to prioritize the response to potential vulnerabilities and ensures that the most severe threats are addressed promptly. To learn more about the specific details and severity levels of Immunefi's security coverage, please refer to the updated documentation available at https://immunefi.com/severity-updated/.
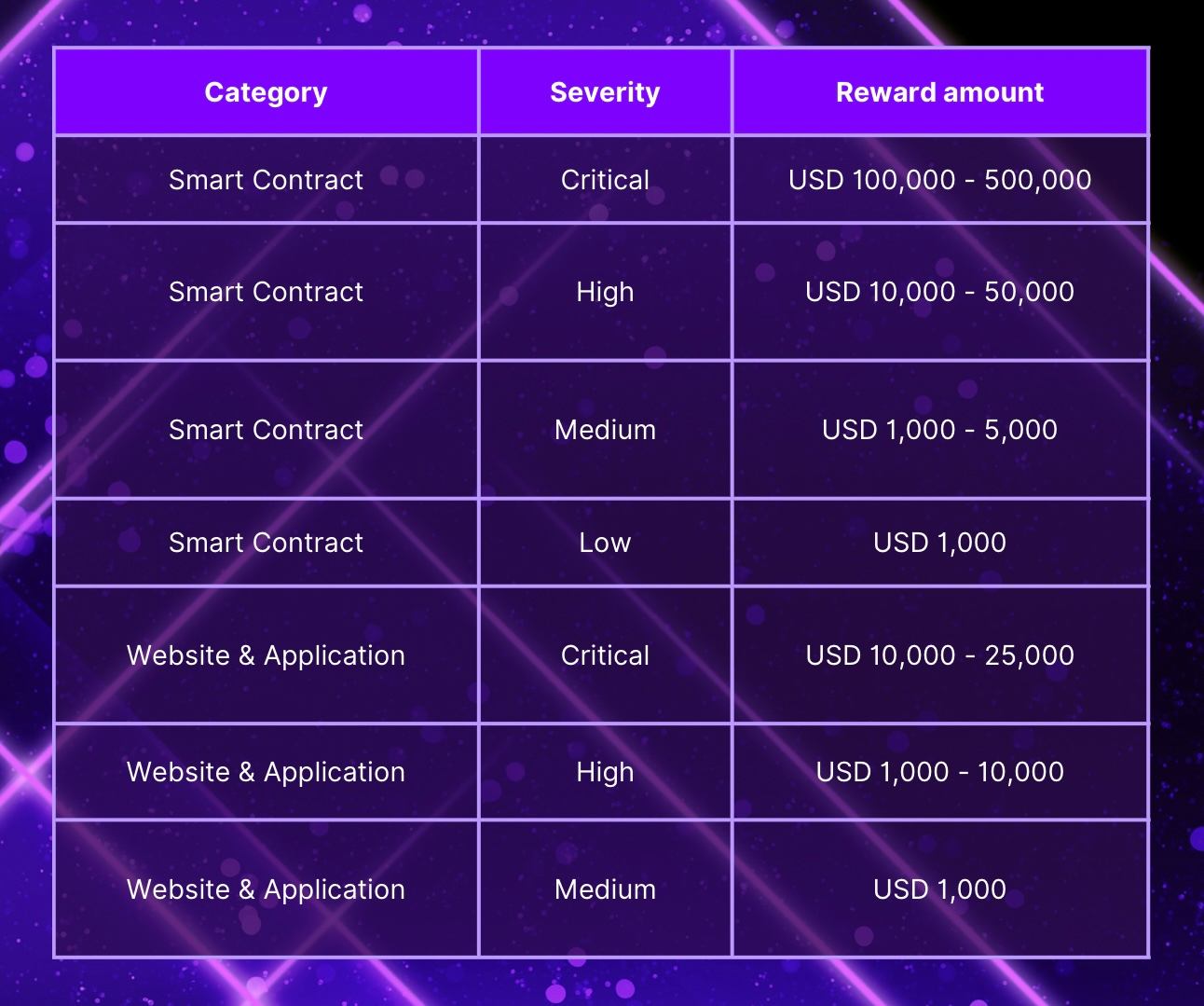
It is highly recommended that white hats review the details of this program in full. Although many bug bounty programs have standard terms and conditions, each also has their own unique details that are critical to your success. Prior to submitting a report please review the Immunefi Bug Report Template and Best Practices. For the full information on Immunefi’s coverage of Threshold, please visit https://immunefi.com/bounty/thresholdnetwork/.
Let’s Squish Some Bugs
The importance of security and white hat work in open source protocols cannot be overstated. By working together to identify and fix vulnerabilities, the community can ensure that the protocol is secure, resilient, and able to deliver on its promises.
About the Threshold Network
Threshold is the first ever on-chain merge between two existing networks and communities, Keep and NuCypher. The Threshold Network provides a suite of threshold cryptography products that power user sovereignty on the public blockchain. Threshold cryptography distributes sensitive operations across multiple independent entities, like nodes in a network. A successful operation requires a threshold or a minimum number of entities to cooperate. This simple idea increases security and availability and reduces reliance on trusted parties.Threshold is governed by a DAO whose parts hold separate responsibilities that are embedded in the governance structure. The Threshold DAO has two primary bodies: the Tokenholder DAO (based on the Governor Bravo governance model) and the elected Council. The goal of this two-pronged structure is to enhance representation while ensuring accountability. Each governance body holds the other accountable, similar to the system of checks and balances found in most constitutional governments. For more information about Threshold Network, please visit https://threshold.network/